WTF?!?!?!?..........
For links see article source.....
Posted for fair use.....
http://www.belfasttelegraph.co.uk/t...raffic-rerouted-through-ukraine-31066133.html
UK’s nuclear weapons data and other sensitive internet traffic rerouted through Ukraine
14 March 2015
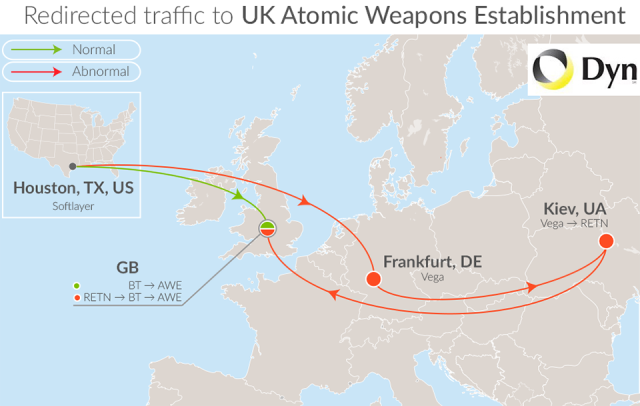
Internet data from the UK’s Atomic Weapons Establishment and other sensitive information was being sent through Ukraine, by mistake, all last week.
As well as the nuclear weapons body, which is “responsible for the design, manufacture and support of warheads for the United Kingdom’s nuclear deterrent”, traffic from the Post Office and elsewhere was accidentally being sent through Ukrainian and Russian addresses.
The BT internet traffic should was being rerouted through Ukrainian internet provider Vega, but security experts believe that the problem was a mistake.
Data would not normally be expected to flow that way, and the diversion through Ukraine is far from the most efficient route.
Fraudulent routing of this kind can allow criminals and other malicious agencies access to data but is relatively easy to do.
Dyn, which discovered the problem in Ukraine, says that since routing is based “entirely on trust, it’s relatively easy to commandeer IP address space that belongs to someone else”.
While most of the traffic that was flowing over the networks would have been encrypted and so wouldn't have been able to be read, users snooping on email traffic would have been able to see the IP addresses — and therefore the company and the potential location — of those involved. It’s impossible to tell whether any data was snooped on or lost as it was rerouted.
As well as endangering the security of internet users, such problems can also slow down or break internet connectivity. That could cause huge economic damage.
Some of the groups that had their internet rerouted included Virgin Money, Marks and Spencer and a range of UK government bodies, according to Dyn. Lockheed Martin, the US defense contractor, was also reportedly caught up in the rerouting with VPN service they were running.
The full trace route is below.
Trace from Houston, TX to Atomic Weapons Establishment at 03:22 Mar 12, 2015.
"1. *
2. 173.193.118.140 ae12.dar02.sr02.hou02.networklayer.com 2.948
3. 50.97.18.246 ae9.bbr02.sr02.hou02.networklayer.com 0.3
4. 173.192.18.220 ae3.bbr02.eq01.dal03.networklayer.com 8.133
5. 173.192.18.135 ae1.bbr01.tl01.atl01.networklayer.com 28.524
6. 173.192.18.152 ae0.bbr01.eq01.wdc02.networklayer.com 42.033
7. 173.192.18.195 ae7.bbr02.eq01.wdc02.networklayer.com 40.167
8. 50.97.18.215 ae0.bbr01.eq01.ams02.networklayer.com 118.838
9. 50.97.18.217 ae0.bbr02.xn01.fra01.networklayer.com 124.983
10. 50.97.18.218 ae7.bbr01.xn01.fra01.networklayer.com 124.133
11. 80.81.194.177 edge-3-2-5-231.kiev.ucomline.net 154.988
12. 87.245.247.157 ae2-241.RT.NTL.KIV.UA.retn.net 155.174
13. 87.245.233.238 ae2-10.RT.TC2.LON.UK.retn.net 158.221
14. 195.66.224.10 linx1.ukcore.bt.net 161.442
15. 194.72.31.130 (BTnet inter-pop routes, GB) 166.986
16. 62.172.103.89 core1-pos1-1.birmingham.ukcore.bt.net 163.205
17. 62.6.196.70 vhsaccess1-pos7-0.birmingham.fixed.bt.net 164.139
18.132.153.3.254 (Atomic Weapons Establishment, GB) 177.4 "

For links see article source.....
Posted for fair use.....
http://www.belfasttelegraph.co.uk/t...raffic-rerouted-through-ukraine-31066133.html
UK’s nuclear weapons data and other sensitive internet traffic rerouted through Ukraine
14 March 2015
Internet data from the UK’s Atomic Weapons Establishment and other sensitive information was being sent through Ukraine, by mistake, all last week.
As well as the nuclear weapons body, which is “responsible for the design, manufacture and support of warheads for the United Kingdom’s nuclear deterrent”, traffic from the Post Office and elsewhere was accidentally being sent through Ukrainian and Russian addresses.
The BT internet traffic should was being rerouted through Ukrainian internet provider Vega, but security experts believe that the problem was a mistake.
Data would not normally be expected to flow that way, and the diversion through Ukraine is far from the most efficient route.
Fraudulent routing of this kind can allow criminals and other malicious agencies access to data but is relatively easy to do.
Dyn, which discovered the problem in Ukraine, says that since routing is based “entirely on trust, it’s relatively easy to commandeer IP address space that belongs to someone else”.
While most of the traffic that was flowing over the networks would have been encrypted and so wouldn't have been able to be read, users snooping on email traffic would have been able to see the IP addresses — and therefore the company and the potential location — of those involved. It’s impossible to tell whether any data was snooped on or lost as it was rerouted.
As well as endangering the security of internet users, such problems can also slow down or break internet connectivity. That could cause huge economic damage.
Some of the groups that had their internet rerouted included Virgin Money, Marks and Spencer and a range of UK government bodies, according to Dyn. Lockheed Martin, the US defense contractor, was also reportedly caught up in the rerouting with VPN service they were running.
The full trace route is below.
Trace from Houston, TX to Atomic Weapons Establishment at 03:22 Mar 12, 2015.
"1. *
2. 173.193.118.140 ae12.dar02.sr02.hou02.networklayer.com 2.948
3. 50.97.18.246 ae9.bbr02.sr02.hou02.networklayer.com 0.3
4. 173.192.18.220 ae3.bbr02.eq01.dal03.networklayer.com 8.133
5. 173.192.18.135 ae1.bbr01.tl01.atl01.networklayer.com 28.524
6. 173.192.18.152 ae0.bbr01.eq01.wdc02.networklayer.com 42.033
7. 173.192.18.195 ae7.bbr02.eq01.wdc02.networklayer.com 40.167
8. 50.97.18.215 ae0.bbr01.eq01.ams02.networklayer.com 118.838
9. 50.97.18.217 ae0.bbr02.xn01.fra01.networklayer.com 124.983
10. 50.97.18.218 ae7.bbr01.xn01.fra01.networklayer.com 124.133
11. 80.81.194.177 edge-3-2-5-231.kiev.ucomline.net 154.988
12. 87.245.247.157 ae2-241.RT.NTL.KIV.UA.retn.net 155.174
13. 87.245.233.238 ae2-10.RT.TC2.LON.UK.retn.net 158.221
14. 195.66.224.10 linx1.ukcore.bt.net 161.442
15. 194.72.31.130 (BTnet inter-pop routes, GB) 166.986
16. 62.172.103.89 core1-pos1-1.birmingham.ukcore.bt.net 163.205
17. 62.6.196.70 vhsaccess1-pos7-0.birmingham.fixed.bt.net 164.139
18.132.153.3.254 (Atomic Weapons Establishment, GB) 177.4 "
Last edited: